Vulnerability Counting misses the point
In a summary report by a researcher from GFI Software, a security products company, we learned yesterday that the count of vulnerabilities discovered in 2014 was up over the previous year.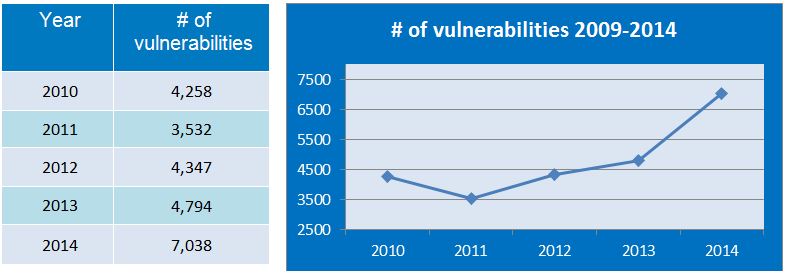
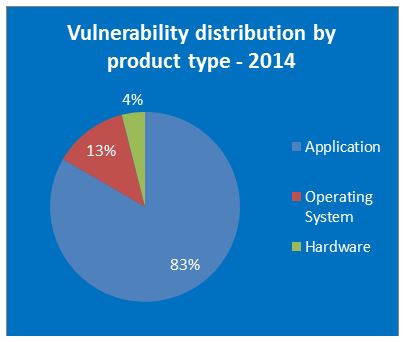
We got a lot of graphs.
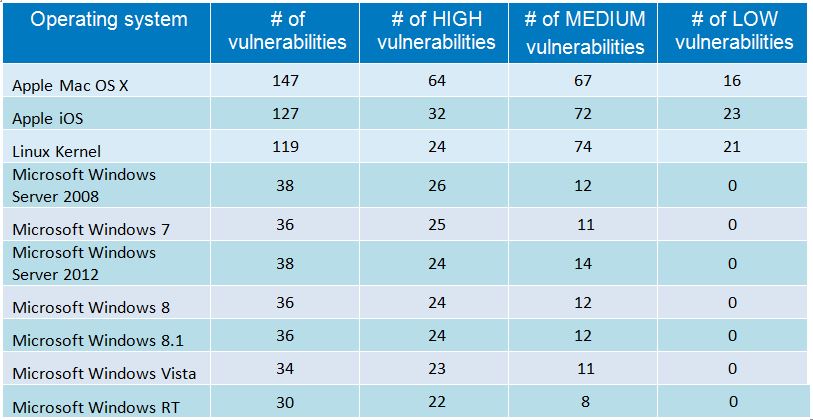
We got tables, too.
OSX and Linux make disturbingly large ripples in the pool, for once.
But all this rather misses the point.
The counts of the vulnerabilities researchers have discovered in your software are only one factor in your overall security picture, and I would argue, a relatively minor one. Most attacks succeed because of misconfigurations and human factors. Malicious insiders and social engineering.
The vast majority of technologically vulnerable software is on machines that should not be accessible from the Internet, and perhaps not even from the majority of the company's intranet. And yet audit after audit will find default-allow access rules, especially on internal firewalls. These, plus lousy defaults for on-the-box controls create many times more opportunities for attackers than should exist.
And for the most part, human failures are really design failures. IT architects design systems with an unspoken and largely unexamined assumption that the operators of those systems will do things correctly. This assumption is one that we security practitioners must challenge at every turn. Two things that security uber-consultant Bruce Schneier has said stick with me. The first is about the fact that good security people are people who break stuff, by breaking the assumptions under which they are designed. For example, here he wrote about a hilarious product called SmartWater, which is water with microscopic particles in it that provide a unique coding, to mark property as yours. Schneier said, "The idea is for me to paint this stuff on my valuables as proof of ownership. I think a better idea would be for me to paint it on your valuables, and then call the police." This should have given the architects of the whole SmartWater idea what we like to call an, Oh, $#!+ moment.
And the second one might be his most-quoted one-liner: "If you think technology can solve your security problems, then you don't understand the problems and you don't understand the technology."
Ultimately, vulnerability counts are about nitpicking the technology. Good technology is important, and we should be pushing the manufacturers to make it better for security all the time. But getting the numbers on all those charts and graphs to zero won't be the final answer.
And the second one might be his most-quoted one-liner: "If you think technology can solve your security problems, then you don't understand the problems and you don't understand the technology."
Ultimately, vulnerability counts are about nitpicking the technology. Good technology is important, and we should be pushing the manufacturers to make it better for security all the time. But getting the numbers on all those charts and graphs to zero won't be the final answer.