Data Breaches Happen to Everyone
The question is, how will you respond?
Verizon just released its annual, much anticipated Data Breach Report (at least peruse the executive summary if not the full report). This year they had a close-to-home item for their report: their own data breach, which resulted in the leak of some 1.5 million of their own customers' records.
There's one thing that does not surprise me, and it's because I make my living in Information Security and don't watch CSI:Cyber. It's that most attacks -- most successful attacks -- against information infrastructures are not enabled by superior technological feats, genius hackers or 0-day vulnerabilities. The plurality (at least) of successful attacks result from this forehead-slapper of an obvious sequence:
- Employee responds to a phishing email by clicking on one of its links
- Malware is installed on said employee's computer
- Attacker leverages the foothold thus provided and the result winds up on pastebin
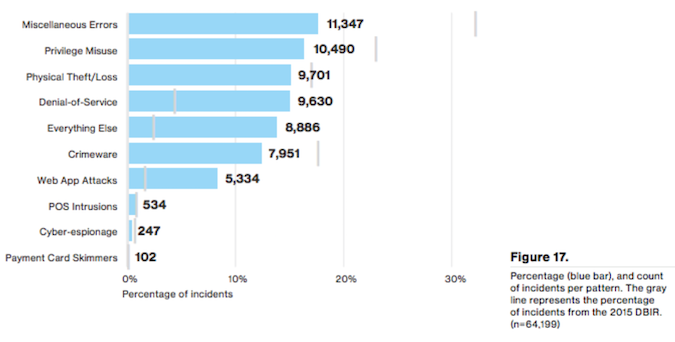
There are some variations on the theme but the result is depressingly the same every time. Unless an organization has a resilience and a defense-in-depth approach baked into everything, they are much more likely than not to wind up fighting a rearguard action and repairing damage rather than preventing it.
It's a truism among information security folks: first, train everyone. The absolute priority of an infosec manager's budget should be awareness training for all the employees. No fancy next-generation firewalls or behavioral-analysis anti-malware can take the place of the admin who just Does. Not. Click. On. Dodgy. Links.

